Shell Control Box is an activity monitoring appliance that controls privileged access to remote IT systems, records activities in searchable, movie-like audit trails, and prevents malicious actions. SCB is a quickly deployable enterprise tool with the widest protocol coverage on the market. It is completely independent from clients and servers – integrating seamlessly into existing infrastructures.
Strong Authentication and Authorization
- Gateway authentication
- Integration with central authentication databases (for example, Microsoft AD, LDAP or RADIUS)
- User-mapping policies – describe who can use a shared user (e.g. “root”) to access the remote server
- Password vaulting – use the built-in Credential Store, or integrate with a third-party password management system
- Server-side auto-login with SCB impersonating the authenticated user on the server
- “4 eyes” authorization – the authorizer can allow, track, and even terminate the administrator’s access to the server
Real-time Alerting and Blocking
- Send an e-mail or SNMP alerts about the event
- Immediately terminate the connection
- Log the event in the system logs
- Store the event in the connection database of SCB

Granular Access Control
- Support for SSH, RDP, HTTP(s), Citrix ICA, Telnet, TN3270, VNC, X11 and VMware View protocols
- Control protocol specific channels, such as terminal sessions, disk-mapping or file sharing
- Audit SCP, SFTP and HTTP(s) based file transfers
- Detailed access control based on time and user group policies
High Quality Audit & Forensics
- Complete documentation about ALL remote system accesses X11 and VMware View protocols
- Tamper-proof (encrypted, signed and time-stamped) audit trails
- Movie-like playback of recorded sessions
- Fast, free-text search in sessions
- Custom activity reports
Smooth Integration
- Independent network appliance, agentless design
- Multiple operation modes
- Fast deployment (3-5 days) and low OPEX
- High Availability option
- Robust hardware configurations
- VMware & MS Hyper-V virtual appliance option
Easy-to-use GUI
- Granular access control to SCB GUI
- User-friendly, web-based search interface
LIBERMAN
Privileged identities are accounts that hold elevated permission to access files, install and run programs, and change configuration settings. These keys to your IT kingdom exist on virtually every server and desktop operating system, business application, database, Web service, and network appliance in your organization.

Business Value of Privileged Identity Management
Taking control of privileged identities can help your organization:
- Reduce IT staff workloads
- Improve IT governance
- Lower cost and uncertainty of IT regulatory compliance audits
- Mitigate risks
Controlling Privileged Account Access
Enterprise Random Password Manager (ERPM) from Lieberman Software can help your organization’s privileged account management through a four-part I.D.E.A. process:
- Identify
- Delegate
- Enforce
- Audit
ERPM continuously discovers, strengthens, monitors and recovers local, domain and process account passwords in the cross-platform enterprise. It identifies, secures and manages theprivileged identities found throughout your IT infrastructure, including:
- Super-user login accounts
- Service accounts
- Application-to-application
Risks of Unsecured Privileged Identities
Privileged identities aren’t controlled by your identity access management (IAM) system, so in all likelihood:
- You do not know of all the privileged logins that exist on your network;
- You have no record of which privileged credentials are known to different individuals;
- You have no proof of who has used privileged logins to gain access to any of your IT resources, when, and for what purpose;
- There is no way to verify that each of your privileged account passwords are cryptographically strong, are sufficiently unique, and are changed often enough to be secure;
- You have no reliable list of privileged logins stored within your applications, and no way to know which in-house and vendor personnel can use these credentials to access sensitive information.
BLUEMOZ (City WiFi, City Airtime, Ibeacon)
- CITY WIFI
- CITY AIRTIME
- IBEACON
Bluemoz hotspot allow to do viral marketing, proximity marketing, geolocalization all in one action, how?
This is the first WiFi hotspot (covered by patent) that works like Wi-Fi access point to “catch your customers”, but at the same time, through the Bluemoz Cloud Free service (= Save Money), you can create important marketing actions!

Our offer it’s easy: an hotspot Wi-Fi, with authentication through Facebook and “Call to Action” of “Like” that allow to surf on internet and Viral Marketing (= Expand your business) through social network; not only Facebook! this technology will be upgraded with Twitter and Google+ using the Gmail account.
“Require us the real statistics about Facebook penetration in your Country, there is evidence that social media affect the sales of assets, just think that 90% of people admit to consider the advice that comes from a friend / acquaintance”.
With the same solution, you can manage the Coupon Gallery that allow instant view of promotions and/or streaming of audio/video files, all managed with an easy web interface – the fast and flexible Bluemoz Cloud – which shows also statistics, upload multimedia files, all in easy way.
This solution can be also integrated with Bluetooth technology for campaign of Proximity Marketing (= Create). This can give an added value if the hotspot is near to parking areas, restaurants/cafè, crossroads with high traffic, etc.
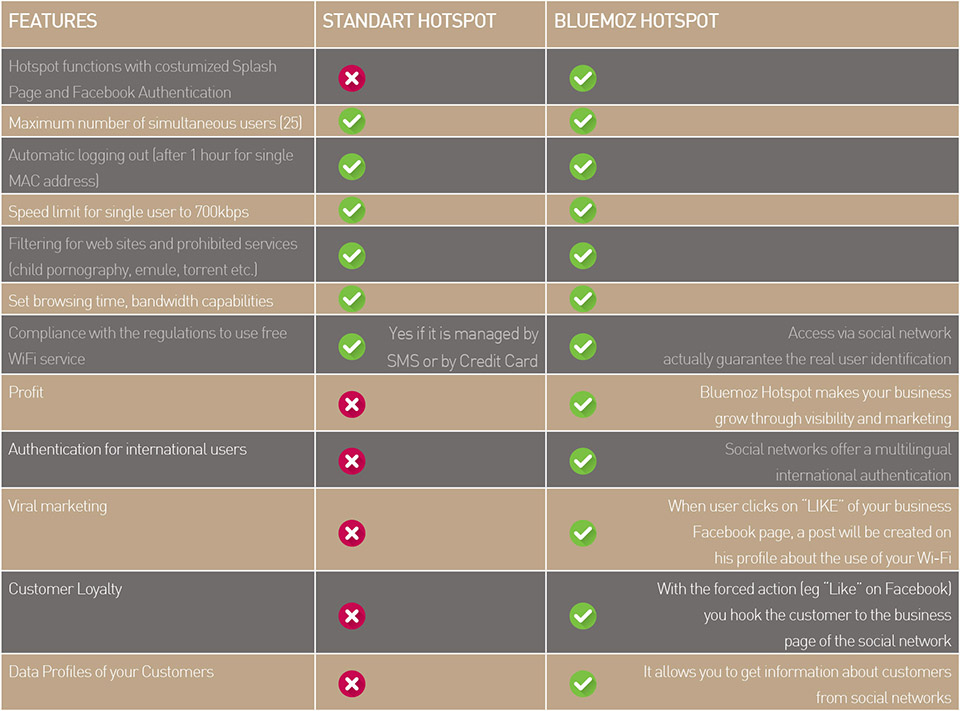
The strengths of the Bluemoz Hotspot systems
- Create a free and easy wireless access point for surfing in Internet.
- Viral marketing: The user click on “Like” of your business Facebook page. This means that every customer who wants to use Wi-Fi has to “Like” the Facebook page which can be seen by all of their friends, the customer will receive in real time your promotions / offers loaded on the Facebook page and all the friends of this customer will receive a message saying that he was at your business, he likes your business and he is surfing through free Wi-Fi. Can happen that, every 100 people who surf through our solution, will generate about 50.000 people informed of your business;
- Simple and Immediate Authentication for people from every nationalities because based on the use of Facebook accounts (international standard) or other international social networks;
- Proximity marketing via Wi-Fi technology: you can upload images or audio/video files on the coupon gallery, this allow an instant viewed from the splash page of your promotions (the splash page is the page where a user will be redirect automatically before authentication).
- Capture profiled informations of your customer, in order to offer promotions to specific targets.
- Differentiate the message for different targets: You can manage more devices installed in different areas, singly or in groups, with the same remote Cloud service to manage;
Comparison table with other Hotspot products
The application related with the area will generate a unique and personal experience for visitors. By connecting their smartphone/tablet to the WiFi hotspot of the service in the area of interest, all visitors will be guided with Audio/Video content in their language. It will also provide access to the various content according to the visitor’s position (different areas with area-specific content).
They will be able to view the area around them through the video camera on their smartphone reproduced in augmented reality of the recreated historical period. Or they can immerse themselves in an augmented reality reproduction of the populated areas in the historical period, again with their smartphone and 3D glasses.

The beacons are small, long life energy bluetooth transmitters. Applications installed on your IPhone or Ipad listen out for the signal transmitted by these beacons and respond accordingly when the phone comes into range.
Our Ibeacon platform offers a wide range or applications that can be applied on an educational context. From simple games that require students to move around, explore and find things to more scientifc or technical experiments in the classroom, iBeacon is a great tool to stimulate young minds and drive curiosity towards subjects like geography, context, automation, logic and technology.

QKLIKVIEW
The QlikView Association (Link Analysis) technology, of which we are a representative, offers an approach of analysis like the human mind thinks. QlikView Business Discovery and Analysis Platform ensures a secure analysis without any limitations. The preparation of data hierarchy eliminates limits such as predefined fixed designs, calculations and summary information. The users are able to ask their questions in random order and receive answers. It provides the users with the opportunity to discover and analyse the questions which does not spring to mind through completely interactive screens.